Describe in Your Own Words How Polyalphabetic Substitution Works
Science relating to the formation and development of words. Bring up the Java Tools.
Vigenere Cipher Automatic Solver Boxentriq
Polyalphabetic substitution definition a system of substitution that mixes together a number of cipher alphabets in a cryptogram so that each plaintext letter is represented by a cipher that repeatedly changes.
. I dont mind talking to him about the project but he is a person who thinks only of himself. A substitution cipher is a type of encryption where characters or units of text are replaced by others in order to encrypt a text sequence. June 11 2012 by Tom Olzak.
The relationship between a character in the plain text and the characters in the cipher text is one-to-one. Please provide reason of your choice in a few sentences or reasons not choosing the other choices. See also the lists in Kimble 2006.
Adjective using several substitution alphabets in turn see multiple-alphabet cipher progressive-alphabet cipher vigenère cipher. You are required to choose the best substitute for the given options. Based on your cipher text you need to make assumptions and replace each letter one by one and then analyze the final result to be sure that your answer makes sense.
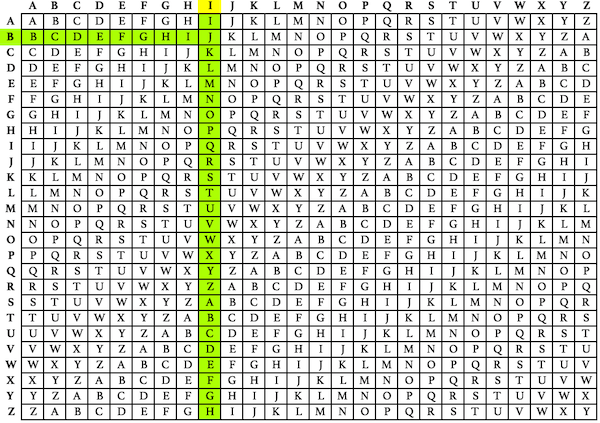
As we have seen in previous chapters security and risk management is data centric. All these techniques have the following features in common. ZEBRAS remaining letters of the alphabet in order.
The idea of using substitution ciphers that change during the course of a message was a very important step forwards in cryptography. Your own privacy is on the line. Please write justification in your own words avoid cut and paste or merely copying the sentences from references.
First I recommend that you download the code for the Java Tools so you can run them locally on your own machine. Substitution ciphers are a part of early cryptography predating the evolution of computers and are now relatively obsolete. Another way to improve on the simple monoalphabetic technique is to use different monoalphabetic substitutions as one proceeds through the plaintext message.
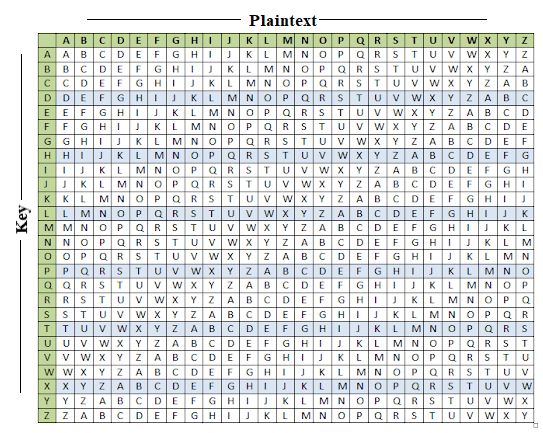
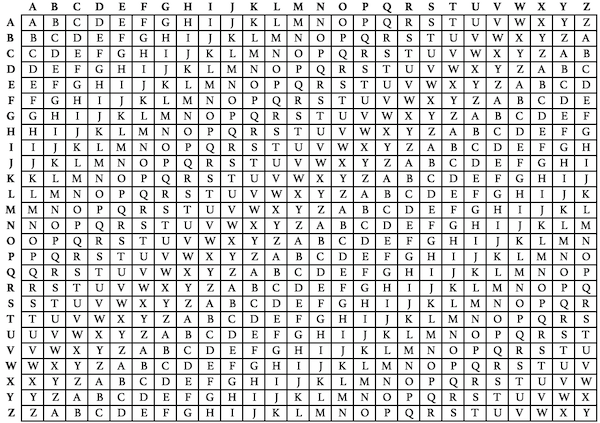
The encryption of the original text is done using the Vigenère square or Vigenère table. To avoid confusion we have categorized the list of one-word substitution into 8 categories. Bold marks the dirty dozen the 12 offenders most likely to weaken your work.
Vigenere Cipher is a method of encrypting alphabetic text. Divert money fraudulently to ones own use. The more correct guesses youll make the more closer you will get and eventually youll be able to crack the final mono-alphabetic code.
Describe in your own words what the Vigenère Cipher. Total 40 Choose the best one. Each list contains 15-40 wordsterms of a particular category.
A polyalphabetic cipher is any cipher based on substitution using multiple substitution alphabets. Before checking on the examples for One Word substitutions lets see how to solve them. How to Solve One Word Substitution.
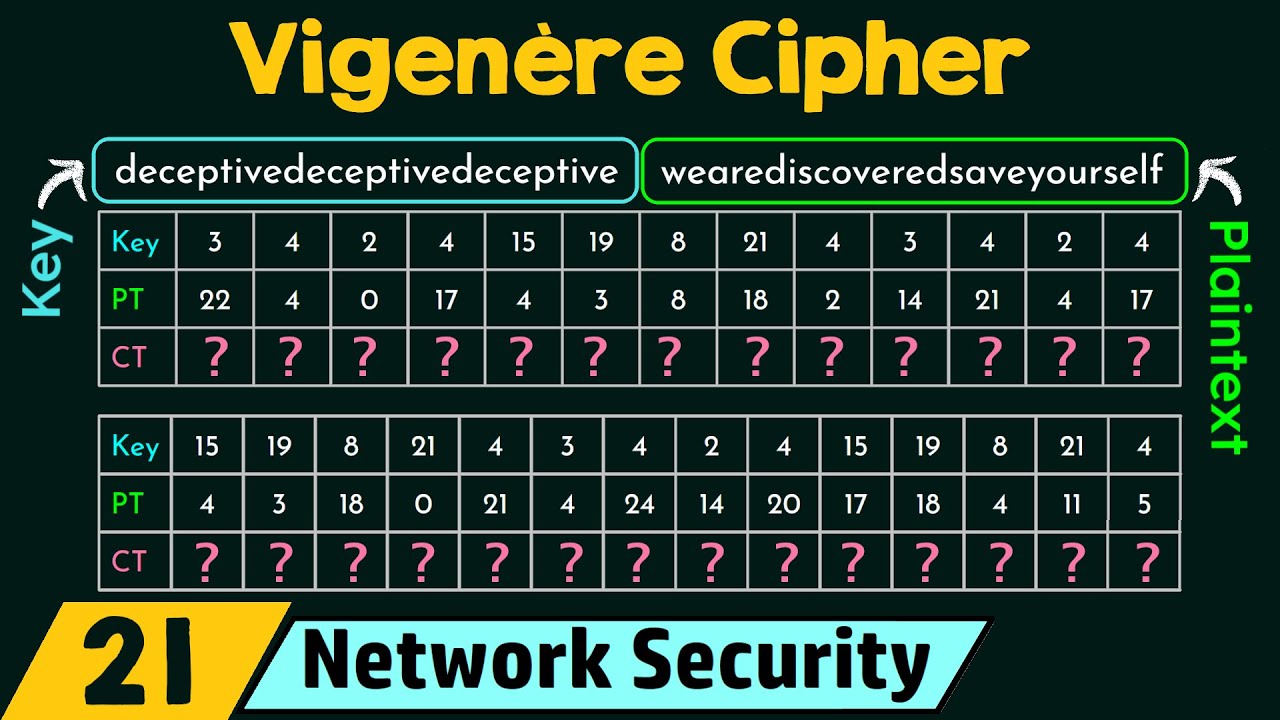
Which discribes the birth of a particular word. To explain how the cipher works lets first replace the characters of the key and the characters of the plaintext by integers where A0 B1 Z25. And select MonoAlphabetic Substitution Cipher.
Honourably discharged from service. Polyalphabetic cipher is any cipher based on substitution using multiple substitution alphabets. Monoalphabetic cipher is one where each symbol in plain text is mapped to a fixed symbol in cipher text.
This will bring up a window which provides you with a lot of tools for cracking a monoalphabetic substitution cipher. These can be solved by identifying its root word or core meaning and then identifying the prefix and suffix. Thus for the key ZEBRAS the ciphertext alphabet would be.
Learn the essential words and enhance your vocabulary. Substitution ciphers work similarly to shift ciphers except you use a key which consists of a word or phrase that appears at the front of your ciphertext alphabet the key should contain no duplicate letters. Network encryption network layer or network level encryption.
There are many lists of complex words and suggested substitutes like the one below. The ommission from a sentence of a work or words that would comple the construction. The network transfer layers are layers 3 and 4.
It uses a simple form of polyalphabetic substitution. After its human resources information is an organizations most important asset. When youre making word choices pick the familiar or commonly used word over the unusual or obscure.
You are presented with the list of most commonly asked one word substitutions. All efforts to protect systems and networks attempt to achieve three outcomes. Now you know that encryption transforms plaintext readable text into ciphertext unreadable text.
The earliest form of polyalphabetic cipher was developed by Leon. If you are describing methodology please describe it in sufficient details so that by following it anybody can reach the same result without additional help from you. Directions For Question 1 to 20 Below given are sentences with highlighted phrases.
Ciphers like this which use more than one cipher alphabet are known as Polyalphabetic Ciphers. Use simple words and phrases. Generally encryption works like that but there are different methods such as symmetric and asymmetric encryption which both take a different approach on how the data is encrypted and how it can be decrypted.
David Kahns book The Codebreakers gives a full account of the origins of this idea during the Italian Renaissance. The key is a string of characters. The role of cryptography in information security.
Many words like Anthropology come from the root word anthrōpos which means humans Here Anthro is the prefix and ology is. Bear Pun Names realistic. The length of the key lets call the period or L.
The general name for this approach is polyalphabetic substitution cipher. Using one-word substitution in this sentence would give something like this My friend chauffeurs me around town. Network encryption sometimes called network layer or network level encryption is a network security process that applies crypto services at the network transfer layer - above the data link level but below the application level.
The Vigenère cipher is a periodic polyalphabetic substitution cipher. In this series of articles you will be acquainted with the concept of one word substitutions. One Word Substitution Questions And Answers PDF- Download PDF Here.
Categories of one-word substitutions. Where Does Grace Murdoch Go To College Vigenere Solver. Part I Each 4 Pts.
Reason must be in your own. If you are describing methodology please describe it in sufficient details so that by following it anybody can reach the same result without additional help from you.
Vigenere Cipher Automatic Solver Boxentriq

Polyalphabetic Substitution Ciphers Crypto Corner

Monoalphabetic Substitution Youtube

Pdf Application Of Polyalphabetic Substitution Cipher Using Genetic Algorithm Semantic Scholar

Polyalphabetic Substitution Ciphers Crypto Corner
Polyalphabetic Cipher Vigenere Cipher Youtube
Types Of Cipher Learn Top 7 Various Types Of Cipher In Depth
Polyalphabetic Substitution Ciphers Crypto Corner

Cryptology Vigenere Ciphers Britannica

Pdf A Simple Algebraic Model Based Polyalphabetic Substitution Cipher
The World According To Benedict Cumberbatch Enigma Chapter 3 The Substitution Cipher

Caesar And Vigenere Ciphers In Microsoft Word Ciphers And Codes Alphabet Code Coding

Polyalphabetic Substitution Ciphers Crypto Corner
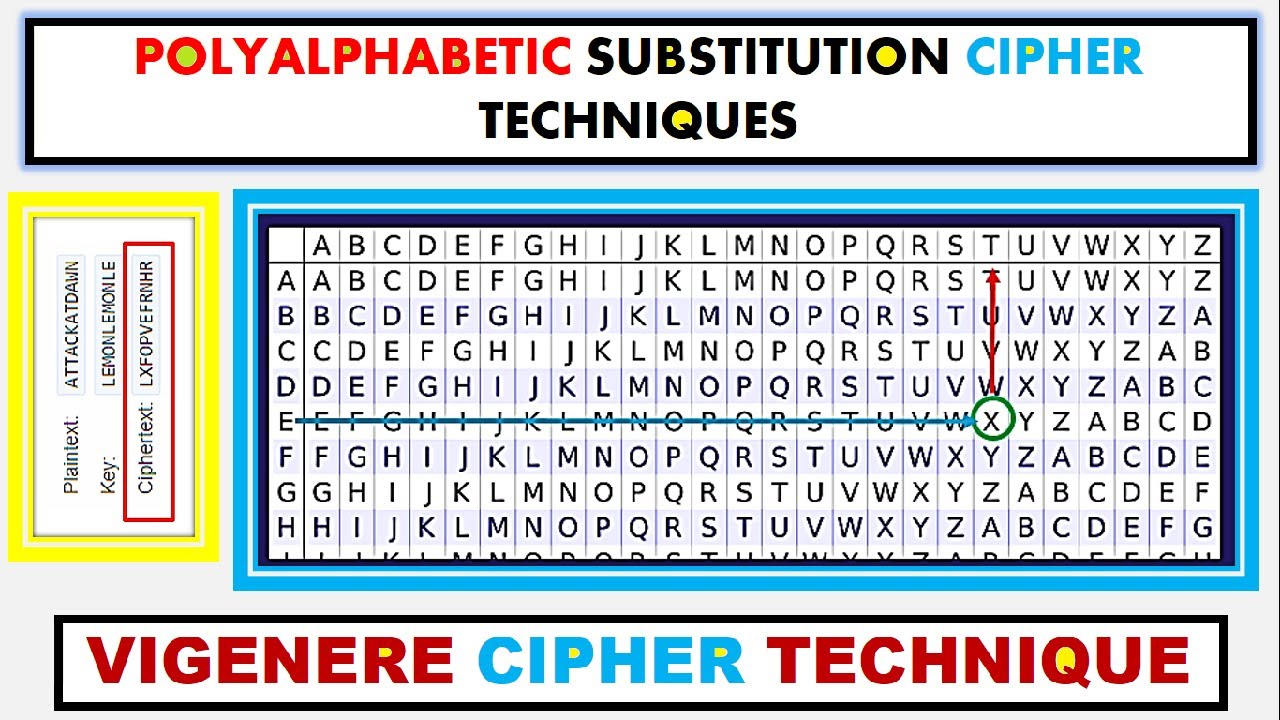
Cryptanalysis Of Polyalphabetic Cipher Such As Vigenere Cipher Xray Pixy Youtube
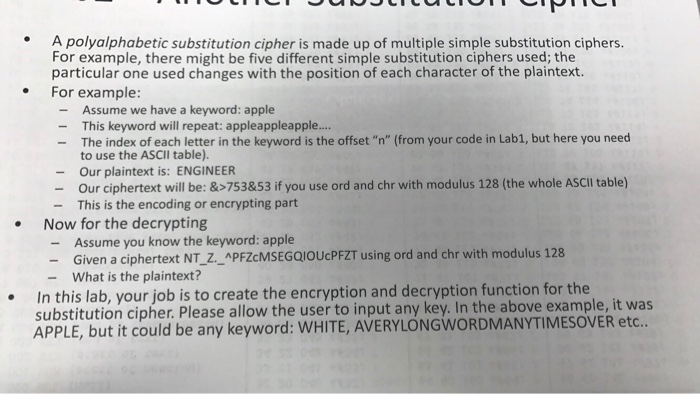
Solved A Polyalphabetic Substitution Cipher Is Made Up Of Chegg Com
The World According To Benedict Cumberbatch Enigma Chapter 3 The Substitution Cipher

Pdf Applying Genetic Algorithms For Searching Key Space Of Polyalphabetic Substitution Ciphers Semantic Scholar

Comments
Post a Comment